
Sensor Networks Group
Software Engineering Programme
Computing Lab
| RED-WSN | ||
Multiple Depth First Search Algorithm In the Multiple Depth First Search (MDFS) algorithm, the protocol that the agents run is a variant of the Depth-First-Search (DFS) one. The main idea is that agents extend the DFS tree with new explored cells in their way downwards, and mark these cells as visited when they traverse them in the opposite upward direction. In the DFS tree the hierarchical relationship between the cells is defined as parent/child. The mechanism used for distributing agents to different parts of the network is as follows: each explored cell has a counter that measures how many agents have traversed it coming from the same parent cell. Note that a cell can be accessed by an agent from at most one parent cell. As agents traverse the DFS tree downwards, they increment the counters associated with each traversed cell. At intersections, they choose to move to the explored cells traversed by the minimum number of agents, so as to assign the same number of agents to each branch of the DFS tree. This algorithms is still not very efficient in terms of exploration time. By definition it traverses each cell at least twice (except for leaf cells), thus resulting in a long exploration time even in open areas without walls where a single traversal would suffice. Brick&Mortar Algorithm Our Brick&Mortar algorithm is designed to address the weaknesses of the MDFS algorithm: unlike MDFS, agents typically traverse each cell less than twice, thus resulting in a shorter exploration time. The driving idea of the Brick&Mortar algorithm is that of thickening the existing walls by progressively marking the cells that surround them as visited. Visited cells are equivalent to wall cells in that they can no longer be accessed. Wall and visited cells are inaccessible cells while unexplored and explored cells are accessible cells. The algorithm aims to progressively thicken the blocks of inaccessible cells, whilst always keeping accessible cells connected. The latter can be achieved by maintaining corridors of explored cells that connect all unexplored parts of the network. Like MDFS, Brick&Mortar does not require agents to know their location in the building. A relocated agent can simply navigate randomly until it finds an accessible cell and then continues the exploration from there. Brick&Mortar makes the blocks of inaccessible cells thicker until the entire terrain is converted to a large block of inaccessible cells. The Brick&Mortar algorithm consists of two discrete steps. In the Marking step, the agent marks the current cell choosing between the explored and visited states. In the Navigation step, the agent decides which cell to go to next.
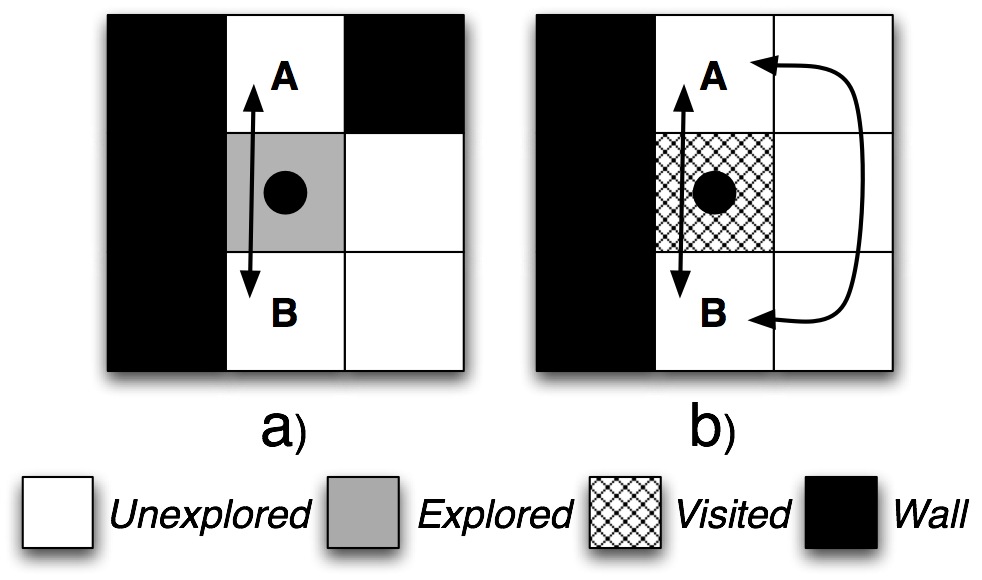 Figure 1: Marking rules: the agent must decide to mark the current cell as explored or visited. In the first example (a) the current cell cannot be marked as visited because it is the only available passage between adjacent cells A and B. In the second example (b) the current cell is marked as visited because there is an alternative passage between A and B on the right.
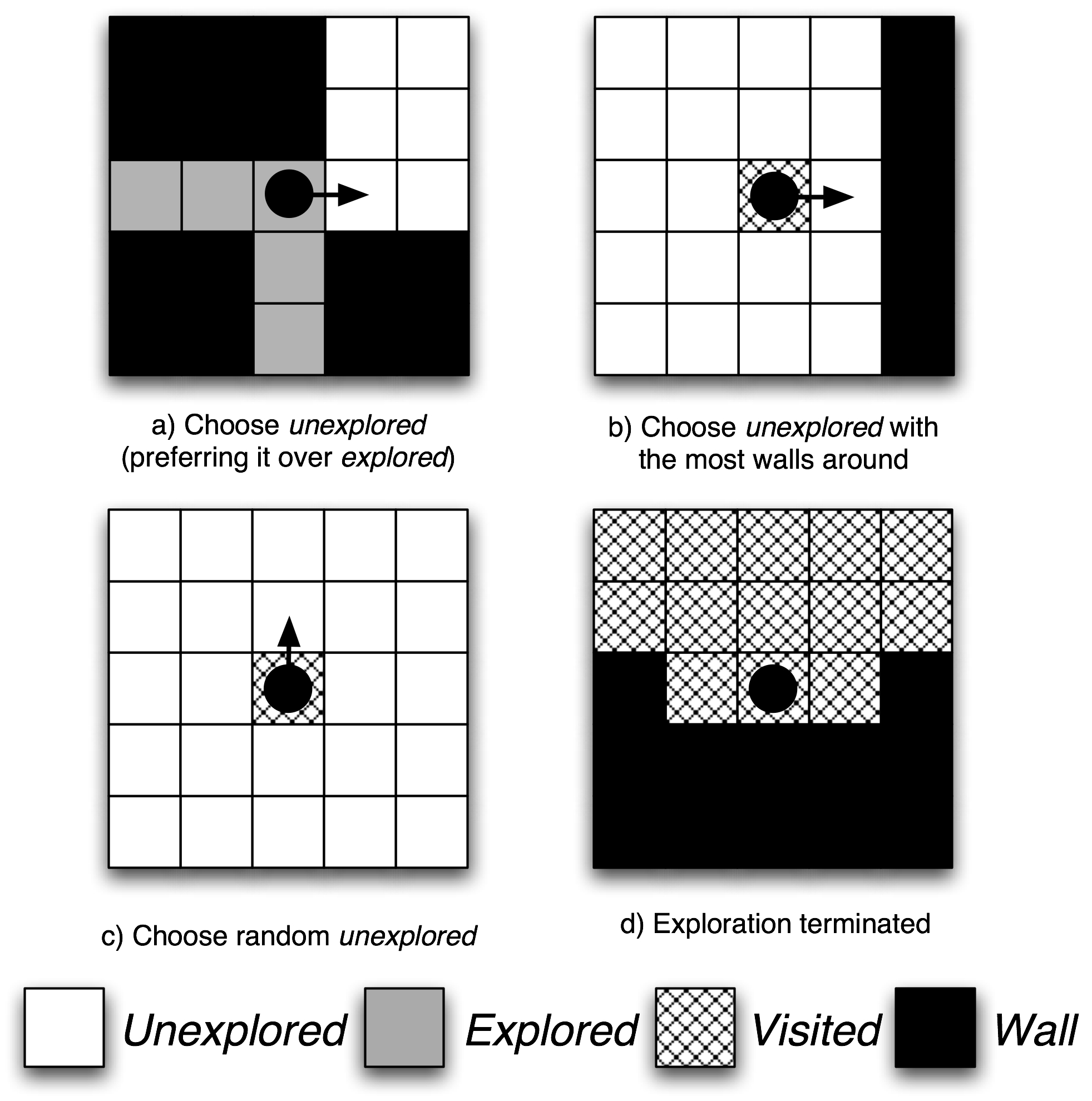 Figure 2: Different situations in which the agent applies the navigation rules to decide which one of the adjacent cells it will go to during the next move. Hybrid Exploration Algorithm The HybridExploration algorithm combines two parallel protocols, one followed by physical agents (robots, or simply agents) and one followed by virtual agents. A physical agent takes significantly longer to move from one cell to another (physical robot motion) than a virtual agent (message propagation). Hence, the time of completing the exploration task is measured as the minimum number of physical steps required by physical agents to explore the entire area.
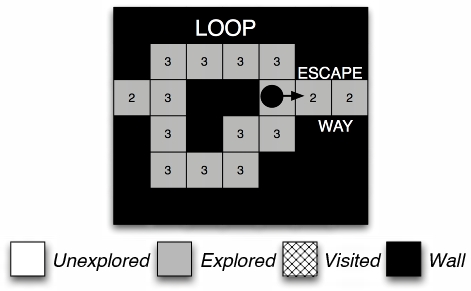 Figure 3: The numbers in the cells represent the times the cell has been traversed in the past. The agent goes to the cell which has been traversed the minimum amount of times to avoid being trapped in a loop.
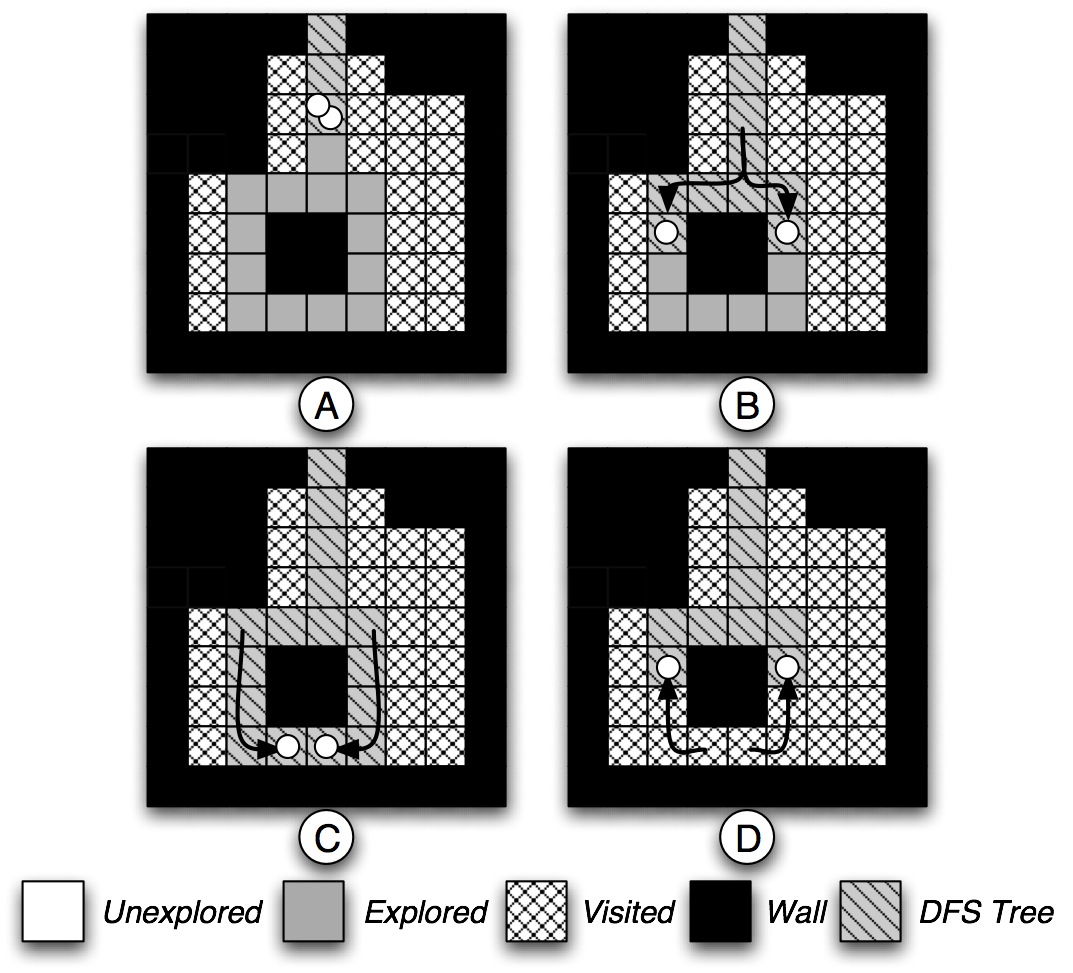 Figure 4: Two virtual agents are collaborating to close a loop left by the physical agents. After the start (A), they separate into each of the two branches of the DFS tree (B) and meet again at the other side of the loop (C). Once there, they do not find any more explored cells which are not part of the DFS tree, so they close the loop by going back and marking every cell as visited . Algorithm for Robot-Assisted Discovery of Evacuation Routes When an emergency occurs within a building, it is crucial to guide victims towards emergency exits or human responders towards the locations of victims and hazards. The objective of this work is thus to devise distributed algorithms that allow agents to dynamically discover and maintain short evacuation routes connecting emergency exits to critical cells in the area. We propose two Evacuation Route Discovery mechanisms, Agent2Tag-ERD and Tag2Tag-ERD, and show how they can be seamlessly integrated with existing exploration algorithms, like Ants, MDFS and Brick&Mortar. We then examine the interplay between the tasks of area exploration and evacuation route discovery; our goal is to assess whether the exploration algorithm influences the length of evacuation paths and the time that they are first discovered. This work is currently under submission, further details will be provided in future. Click here to download a video example. |
||